CRTO review - Red-Team Ops from Zero Point Security
Santa Claus - The original Red Teamer
So, while studying and going through some windows AD concepts, I was looking at how there is some methods for bypassing UAC using fodhelper and etc. so I figured there must be alot of interesting concepts that exist on windows natively but never spoke about or heard about so why not write them here. This approach allows users to escalate their privilege by not only bypassing UAC but also further enhance it with remote code execution (RCE) using netplwiz.
Lets first of all understand what is UAC. It is simply a security feature or a component that exist on windows operating system that allows non-admins to run certain tasks as administrator, just like how we use SUDO in Linux. You would usually get a prompt that asks for your consent to running a task or an application with higher privilege like:
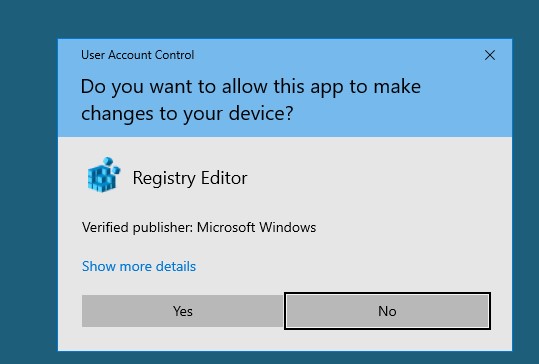
The idea of this is to use netplwiz also known as network places wizard that is commonly used for managing user accounts on windows operating systems. The catch here is this tool runs default on admin privileges and we can easily exploit this policy to obtain admin rights on a system very easily. So lets see how we can do this!
Lets start off by checking what rights we have as a non-admin and an admin using powershell, to give an easier illustration, we can issue whoami /priv command to check the privileges we have as a non-admin user and might have as an admin user on 2 different powershell.
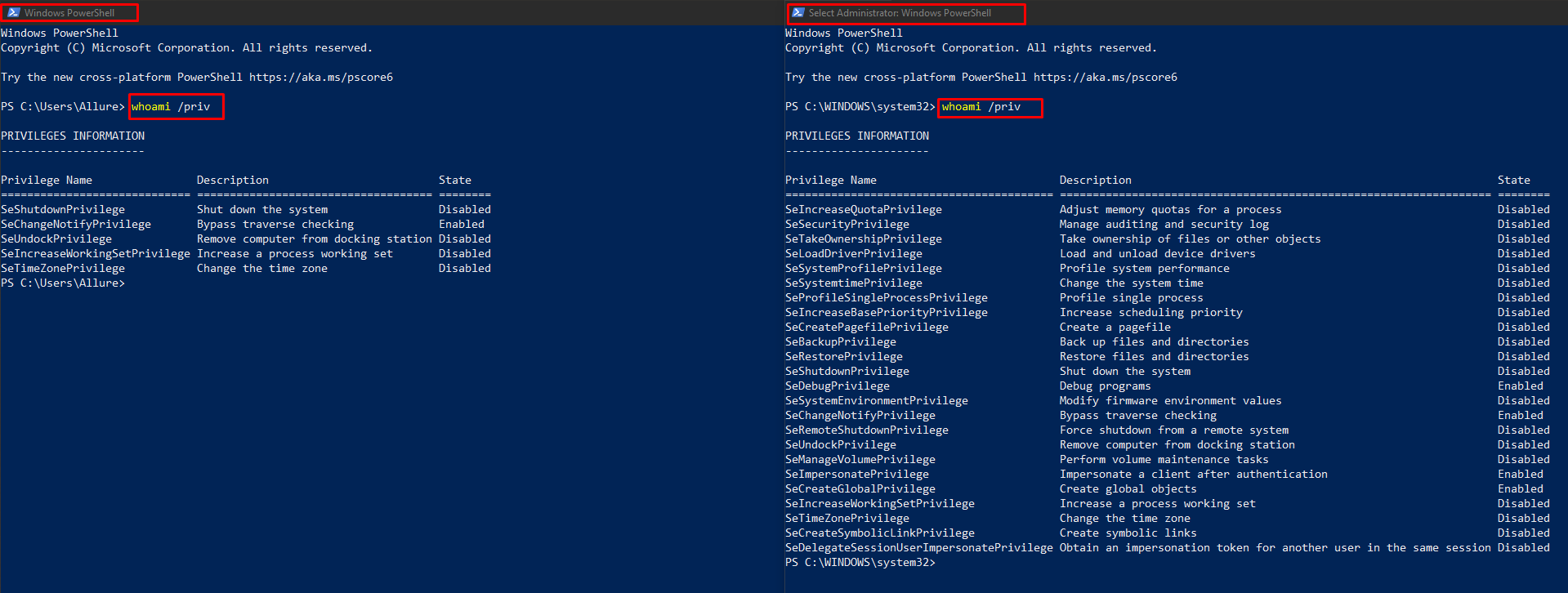
Based on the image above, we can notice obviously that non-admin users on the left side have very restricted amount of privileges onto what they can do compared to an admin with a lot more of privileges on the right side. Being said so, let’s try to see if its actually possible to escalate our non-admin privilege to an admin without really needing to exploit anything.
We can open up netplwiz by searching it and opening as it is without needed to open it as an administrator, as illustrated below:
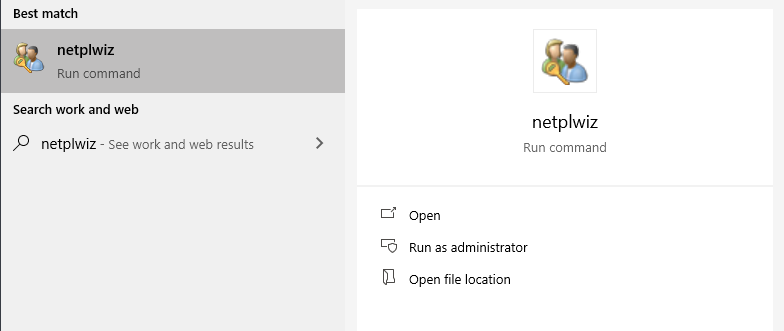
Let’s actually try to understand this for a bit. You might be curious why and how can this tool escalate ones privileges without needing to provide anything? This is simply because netplwiz default runs with admin privileges even if you open it as a non-admin, it works around windows polymorphism where child inherits certain parameters from the parent.
Now that we have netplwiz panel up, we proceed by switching to the Advanced tab and selecting Advanced under Advanced User Management
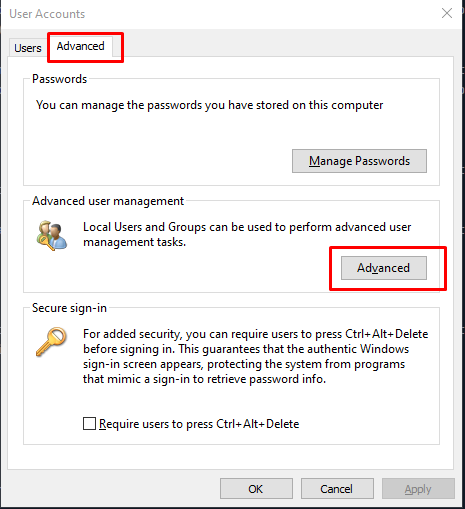
This will open up other panel called lusermgr which basically abbrievates to local user manager.
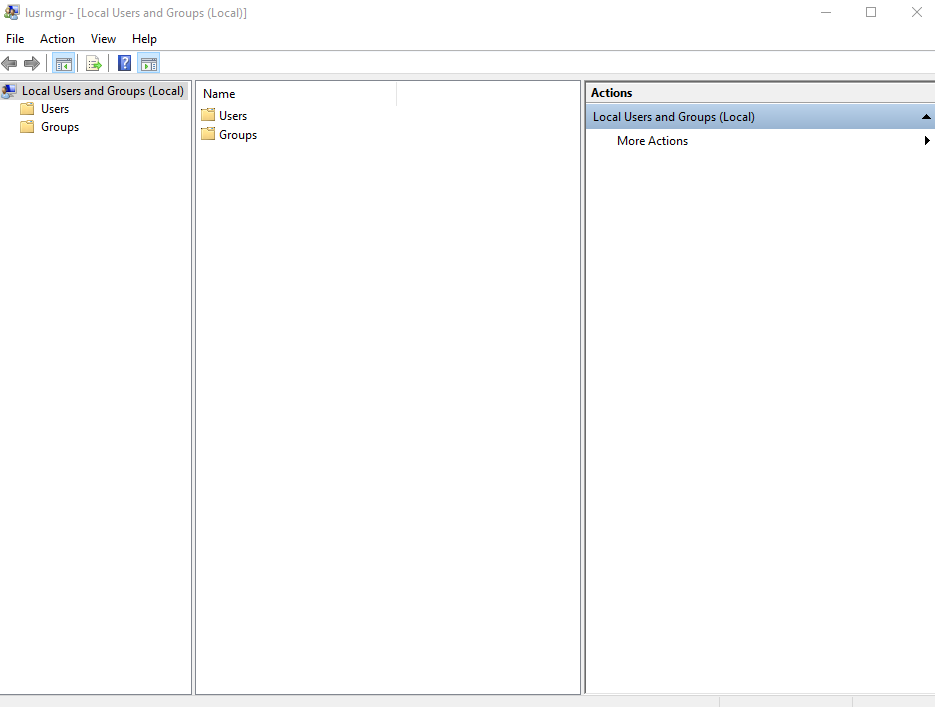
On lusermgr click on the HELP tab and select help topics
This opens up a Microsoft Management Console page which is a CHM file that exist on Windows Operating system that is used for compiling documentations in HTML format.
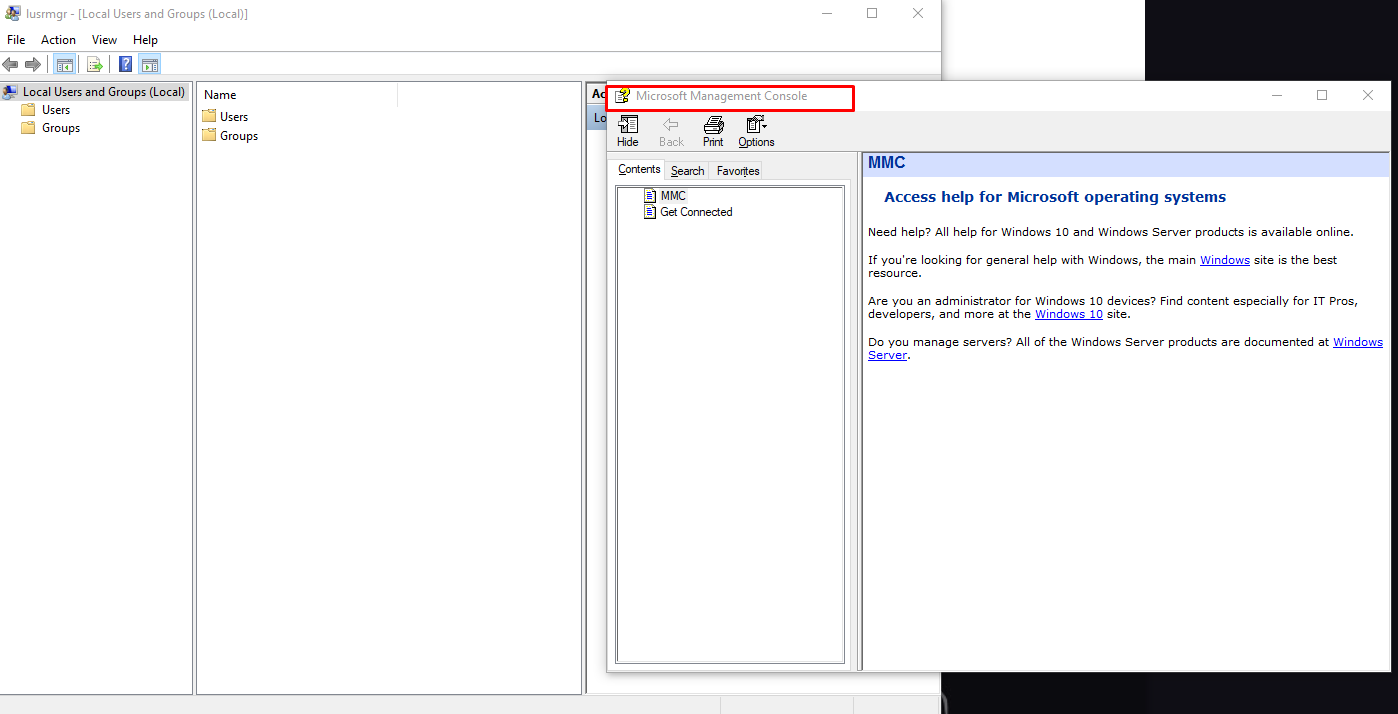
Well well, do you see what’s very exploitable here or figured it out yet?! That’s right the caveat is that this CHM file indeed is in HTML format like web-pages where we can view source!
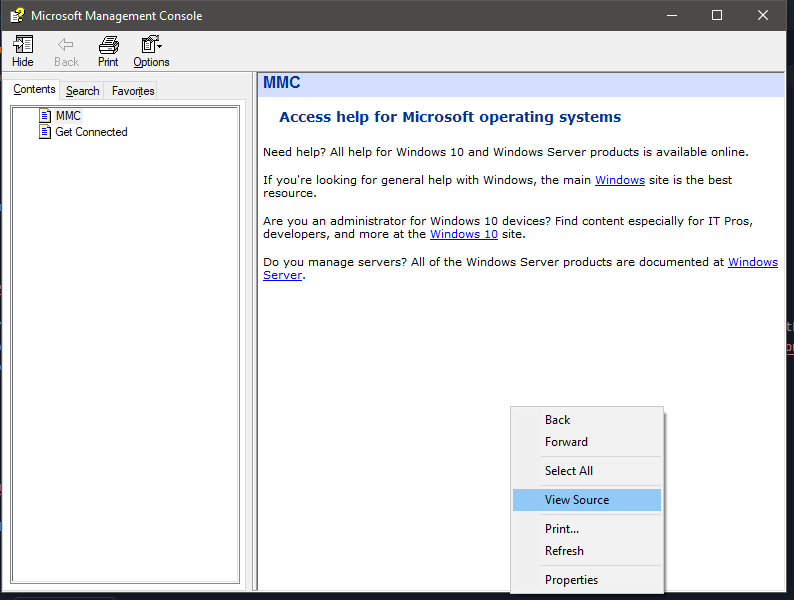
Now you can see, from the above step we can view the HTML source in our notepad, and this from an attacker mindset only means one thing, its very exploitable!
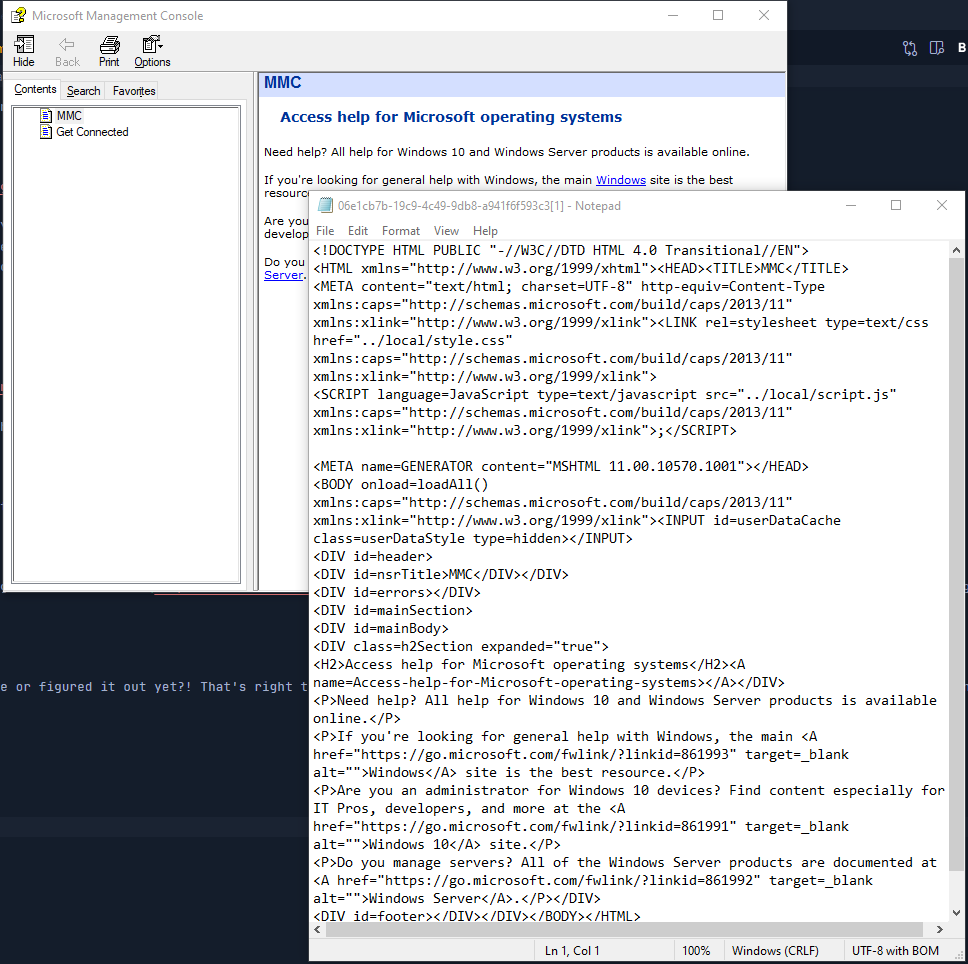
With that being said.. we have a great vector where we can open literally just about anything from a notepad using it’s standard features, so instead of just opening any malicious script, why not try to open an application? PUTS ON HACKER CAP
For that, we will click on File and select open which will prompt a GUI. Make sure to enable All files and navigate to the directory where cmd.exe usually is located on (this might vary for users), as illustrated below:
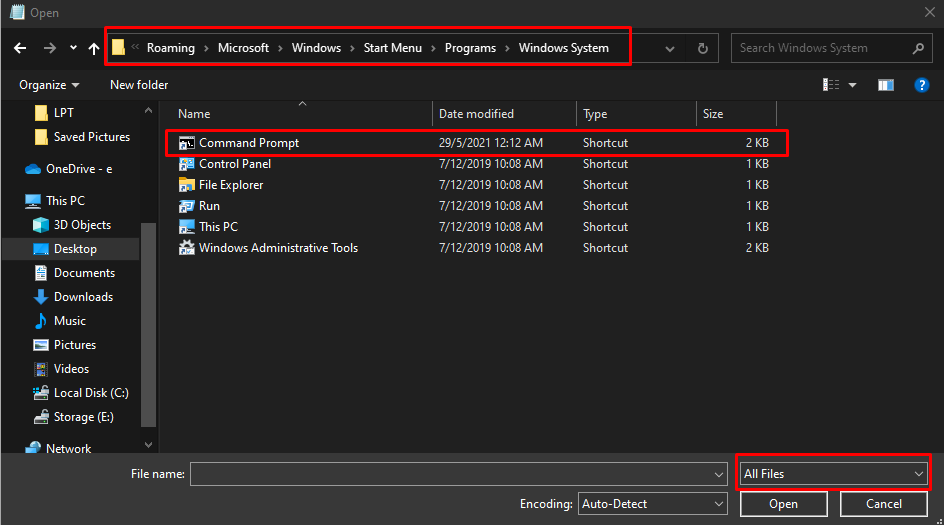
Here we are, looking at something pretty cool, a command prompt.exe. Instead of opening it like a normal user we right click on command prompt.exe and select ‘open’ and voila!
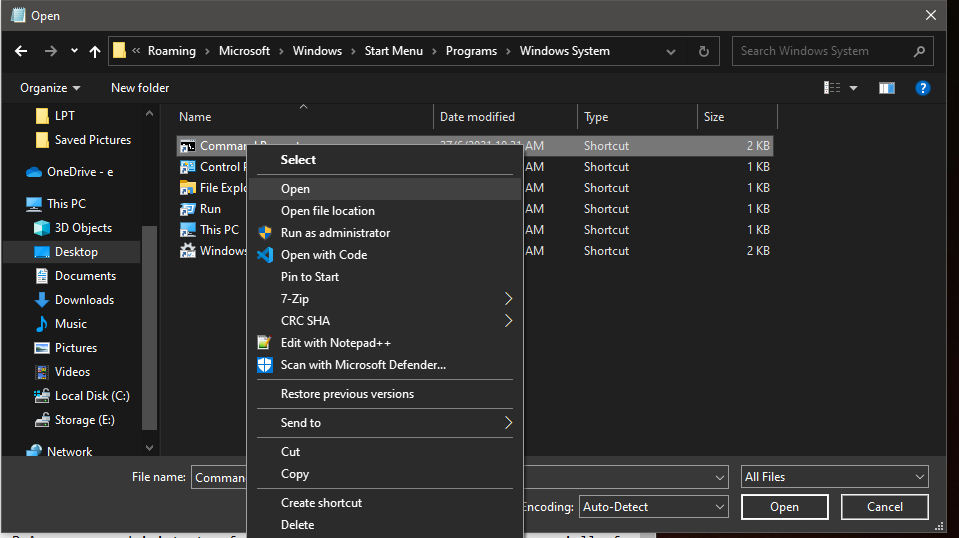
We have managed to open a command prompt with admin privileges which just about gets us anywhere on a windows operating system, most importantly we can perform RCE’s!
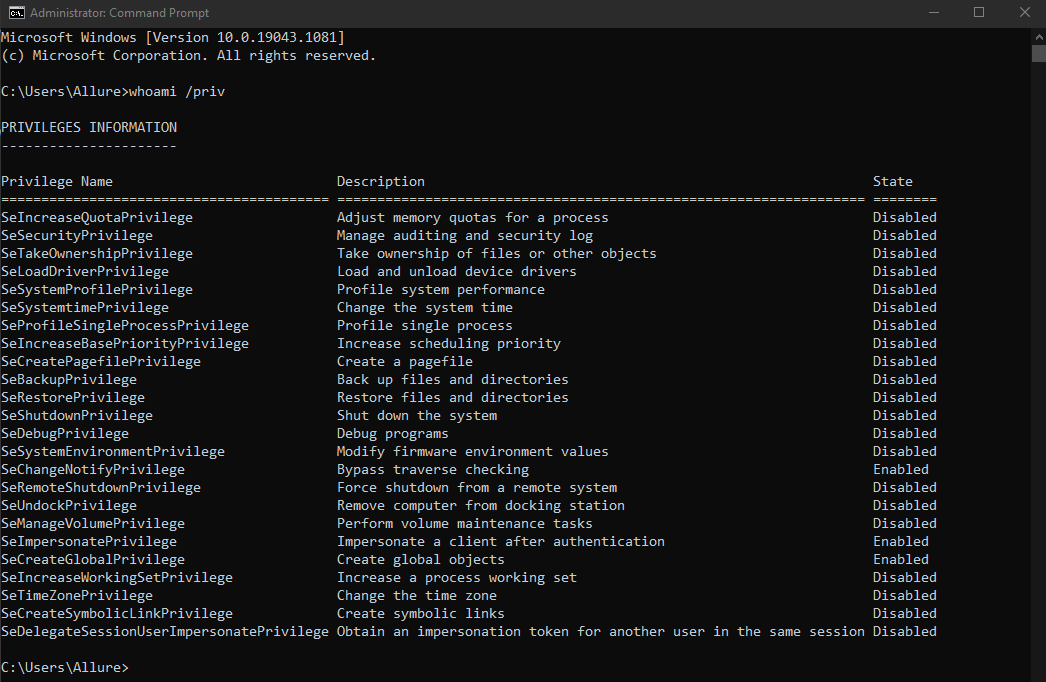
We started off as a normal user or aka non-admin user and abused the inheritance policy on netplwiz by exploiting CHM files to redirect to opening a command prompt in admin privilge. This is a very interesting vector for privilege escalation which usually can lead to RCE’s and systems go BOOM!!
Obviously there is alot more methods out there in the wild that exist for these sort of UAC bypasses and privilege escalation but I really liked this one as I have personally used it for my CRTP exam as well.
I hope you enjoyed this short post and many more to come!
